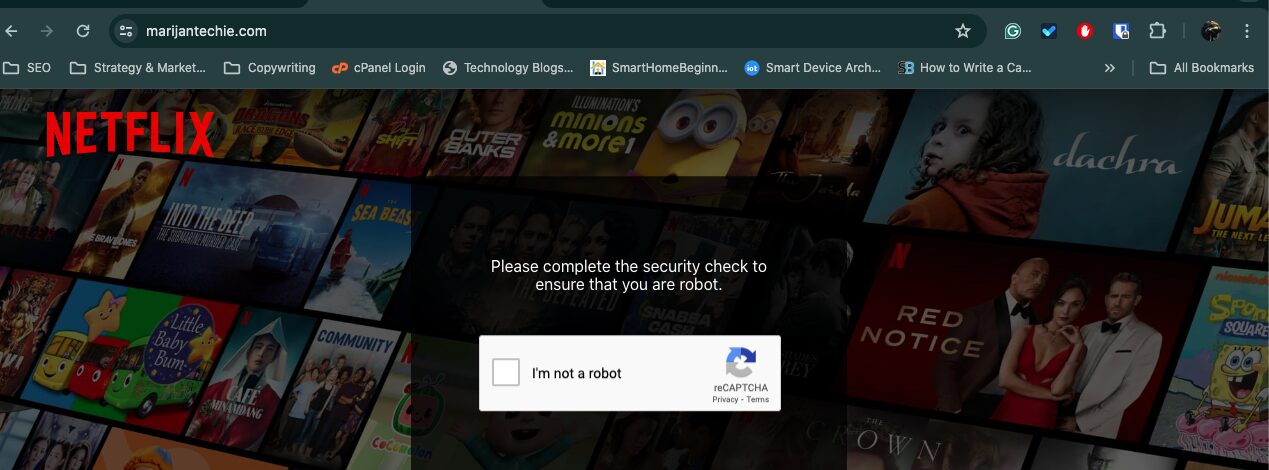
A while back, a hacker(s) compromised this website (marijantechie) and redirected it to a fake Netflix page. How did it happen? I gave them the username and password to the website’s control panel. They tricked me and I fell for it.
That’s not what I had imagined as I tried to figure out how they got in. I thought the hacker had exploited a security weakness in my theme or hacked my web hosting provider.
And that’s the thing. When most people think about getting hacked, they imagine the technical and complex side. They see a nerdy-looking person incessantly typing code on their computer until it unlocks the target system – like in the movies.
In real life, it’s much simpler and it can be prevented. Follow along as we explore all the ways hackers can get to you and how to protect yourself.
PS: By hacking I mean someone gets unauthorized access to your online accounts including email, social media, and financial. Business systems like PoS, accounting, and HR software can also be hacked.
1. Social engineering
Social engineering is the collective term for hacking techniques that rely on mind games. In my case, for instance, the hacker sent an email warning that I had almost exhausted my website storage. The email was a lot like the one attached below.
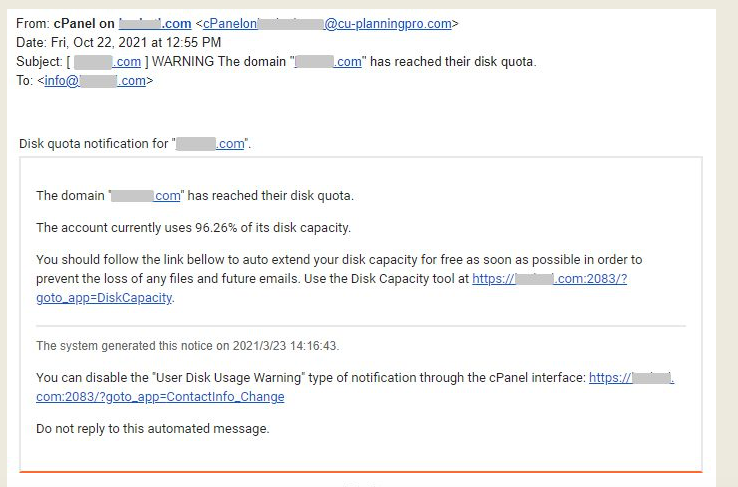
It didn’t make sense because I’ve only published a few articles. Still, I used the link in the email to log in to my website’s control panel. As you might have already guessed, the link took me to a fake website. I thought I was logging in to my control panel but hackers were on the other end harvesting my details.
This technique is called email phishing and it’s the most common form of social engineering. First, the hackers create an imitation of a popular website that requires your login details (Google, Facebook, Instagram, LinkedIn, etc). They then use a clever email to get you to click the link and log in.
Any website can be spoofed. Social engineering can also take the form of calls, SMS, or even direct contact. It depends on how creative the hacker is.
How to protect yourself
Your best protection against social engineering is awareness. By realizing that not every email, message, or even call you receive is legitimate, you can learn to practice caution.
Additionally, always verify the source of login requests. Especially if they involve private information or financial transactions. If a request comes in from a known person but they’re not using the usual contact (email or phone number), that’s a red flag that needs further examination.
2. Stolen credentials
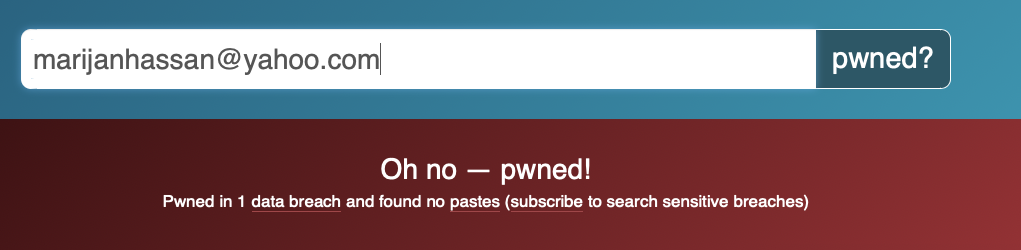
Another way you can be hacked is if your login details are exposed in a data breach. Major companies get hacked all the time. And if they don’t securely store your login details the hackers can steal and sell the information on online forums. Anybody with access to these details can steal your identity and take over your online accounts.
There are multiple websites that you can use to check if your information has been leaked using your email address. One of them is haveibeenpwned. Yahoo, LinkedIn, and Twitter are examples of big names that have been breached in the past.
Unfortunately, in Kenya, there’s no law or regulation requiring that a company disclose to the public when it’s breached. So you might not even know your information has been leaked. There are whispers that a top insurance company was breached, but I haven’t seen it on the news.
How to protect yourself
Now with stolen credentials, you have no control over if your data gets leaked. But, there are two steps you can take to protect your accounts.
- Enable multi-factor authentication. MFA or 2-factor authentication adds an extra layer of security to your online accounts by requiring additional verification to grant access. So, even if a hacker gets your username and password, they need that extra code to access your account. There are different MFA methods and I explore all of them in my other post, How to never get hacked on social media.
- Don’t reuse one password for multiple accounts. This way if one account gets compromised, the hackers can’t use the information to access other accounts.
3. Malware
Malware is short for malicious software. Once installed on your device, it allows the hacker to steal your data (infostealers), take remote control of your device (RAT), or encrypt your files rendering them inaccessible to you (ransomware).
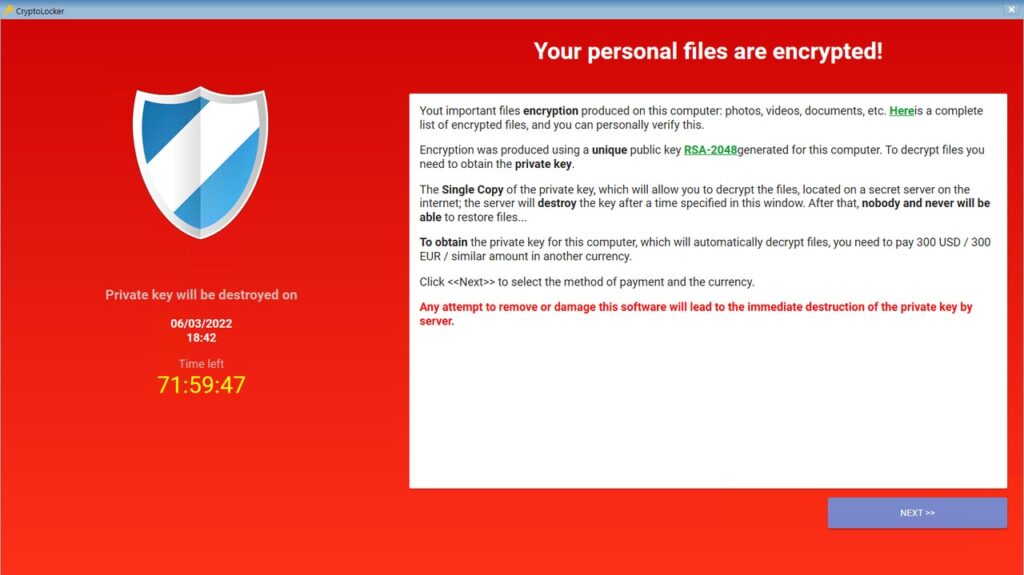
Pirates won’t like this, but one of the most common ways to distribute malware is through cracked software. This method is very effective because most of these cracked tools require that you turn off protection to proceed with installation.
Hackers can also use baiting where they leave a flash drive loaded with malware in a location where it will be found. When the target picks up the item and uses it, malware is installed on their system. Old, but still effective method.
How to protect yourself
I can tell you to avoid using cracked software but we know that’s not possible. The average person doesn’t have thousands to splurge on software licenses every month. So this is a risk you’ll need to accept.
The best you can do is invest in an antimalware solution. Most providers have free versions that will be great for general everyday use. The free versions mostly rely on database signatures meaning they won’t detect a threat unless it’s already been identified and documented. But it’s better than nothing.
Premium security tools come with advanced detection capabilities including behavioral analysis which means they can detect threats by flagging abnormal system behavior. However, unless you’re a business, most times it won’t make sense to invest in a paid antivirus or antimalware.
4. System vulnerabilities
If you’ve ever hard reset your Android phone (it’s called Flashing in the streets), you know it requires your Google account or your screen lock before it can open. This is a security feature that’s supposed to protect your phone against theft.
But if you take it to the repair shop they can bypass the Google sign-in option. How? Usually, it’s by exploiting a security vulnerability in the Android operating system.
Any computer system or software you use has been coded by people, which means chances are high that it has a weakness. Hackers are always scanning for these weaknesses so they can use them.
The good news is most developers are also constantly testing their products for weaknesses and fixing them.
How to protect yourself
Regularly update your software, applications, and operating systems to ensure you have the most secure version.
The Takeaway
Gone are the days when hackers used to only target businesses. Now, everybody is a target. What distinguishes you is whether you’re hard or easy prey. Hacking is opportunistic. If you prove to be too much trouble, the hackers just move on to the next easy target. I just gave you the basics to protect yourself.



Leave feedback about this